In today’s digital era, the risks of data theft, cybercrime, and privacy breaches are ever-present for organisations. It’s crucial for businesses to align their information security strategies with their overall objectives, size, and structure.
ISO 27001 is an international standard developed and published by the International Organization for Standardization (ISO) in collaboration with the International Electrotechnical Commission (IEC) that outlines the requirements for an information security management system (ISMS). This standard provides a systematic approach to managing sensitive company information so that it remains secure. It provides guidance for establishing, implementing, maintaining and continually improving an organisation’s ISMS.
The ISO 27001 standard offers a framework for creating a tailored ISMS, incorporating a scalable risk management process to meet an organisation’s evolving needs. Adopting ISO 27001 enables organisations to address security risks effectively and maintain a robust defence in a constantly changing threat environment.
Benefits of ISO 27001
- Enhanced Security: Implementing ISO 27001 helps in identifying vulnerabilities and putting controls in place to manage or reduce risks.
- Increased Resilience to Cyber Attacks: It provides a framework for building a more robust defence against cyber threats.
- Improved Compliance: It assists in meeting legal and regulatory requirements underlining data protection and privacy.
- Competitive Advantage: Certification can give you a competitive edge by demonstrating to customers and partners your commitment to data security.
- Cost Savings: By identifying and mitigating risks early, organisations can save on costs associated with information breaches.
A critical aspect of the ISO 27001 framework is the identification and treatment of information security risks. This involves:
- Risk Assessment: Identifying information security risks by understanding potential threats, vulnerabilities, and impacts on business operations.
- Risk Treatment Plan: Once risks are identified, organisations develop a Risk Treatment Plan (RTP) to address how each identified risk will be managed. This could involve applying specific controls from Annex A of ISO 27001, deciding to accept the risk if it’s within the organisation’s risk appetite, transferring the risk (e.g., through insurance), or avoiding the risk altogether.
- Implementation of Controls: Selecting and implementing appropriate controls to mitigate identified risks. These controls are chosen based on their effectiveness in reducing risk to an acceptable level and can range from technical solutions (like encryption) to management strategies (like training and awareness programs).
- Monitoring and Review: The RTP is a living document that requires regular review and updates based on the evolving threat landscape, effectiveness of current controls, and changes within the organisation’s operations or assets.
While ISO 27001 compliance is not mandatory for all businesses in Australia, it offers numerous advantages in today’s cyber-threat landscape. Achieving ISO 27001 certification demonstrates a commitment to information security, improves customer trust, and aligns organisations with industry best practices.
Challenges of implementing ISO 27001
While there are considerable benefits to implementing ISO 27001, there are also several challenges that organisations should be aware of, including the need for substantial financial investment and resource allocation. The process demands a thorough understanding of the standard’s requirements, which may require specialised training, as well as new technologies or expertise. Additionally, the organisation must be prepared for the ongoing commitment required for maintaining compliance, involving regular reviews and updates of security practices, internal audits, and external assessments.
Despite these initial expenses, the long-term payoff in terms of enhanced security and trust more than justifies the cost. This is also where Procure Spot can step in to offer expertise, guidance, and support.
The risk of not implementing ISO 27001
Globally, cybercrime’s borderless nature makes it a complex issue, with cyber criminals often collaborating across countries. This scenario calls for businesses to adopt strong, flexible cybersecurity measures and promote a culture of security awareness to counter these threats effectively.
In today’s digital world, Australian businesses face a growing threat from cybercrime. Cyber criminals use advanced methods to launch attacks, such as ransomware, phishing, and data breaches, aiming to steal sensitive information and cause financial and reputational damage.
Australia’s strict data protection laws add pressure on organisations to protect data and comply with regulations like the Australian Privacy Principles and the Notifiable Data Breaches scheme.
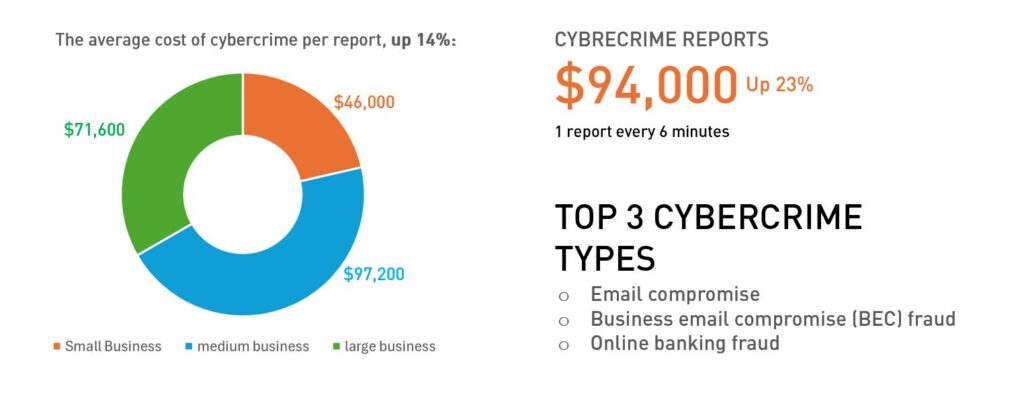
According statistics from the Australian Cyber Security Centre’s (ACSC) Cyber Threat Report 2022-2023:
ISO 27001 Consultant - How Procure Spot can support your organisation in achieving ISO 27001
Procure Spot’s services are tailored to guide your company through the entire process of achieving ISO 27001 certification. We understand the complexities involved and provide comprehensive support to ensure your ISMS meets the requirements. Here are some of the ways in which we can help:
Policy Templates: We offer customisable policy templates that serve as a solid foundation for your ISMS, ensuring that all necessary policies are in place and aligned with ISO 27001 requirements.
Documentation Review: Our experts review your existing information security documentation to identify gaps and areas for improvement, ensuring compliance with ISO 27001.
Gap Analysis: We conduct a thorough gap analysis to understand your current information security practices and how they measure up against ISO 27001 standards.
Risk Assessment Assistance: Our team aids in conducting risk assessments, a critical component of the ISO 27001 process, by identifying, analysing, and evaluating information security risks.
Training and Awareness: We provide training for your employees to enhance their understanding of information security best practices and the requirements of ISO 27001.
Implementation Support: From setting up the ISMS to implementing controls and measures, we offer hands-on support throughout the implementation process.
Pre-certification Audit: Before the official certification audit, we conduct a pre-certification audit to ensure your organisation is fully prepared, and to minimise the risk of non-compliance.
Surveillance audits: Post implementation, we offer surveillance audits with a third-party certifier to ensure you remain compliant.
Achieving ISO 27001 certification is a significant step towards ensuring that your organisation’s information is securely managed. Procure Spot is committed to providing the support and expertise needed to navigate the complexities of ISO 27001, from initial gap analysis to certification. With our help, you can demonstrate your commitment to information security, gain a competitive edge, and build trust with stakeholders.
Contact Procure Spot today support@procurespot.com to start your journey towards ISO 27001 certification and take your organisation’s information security to the next level.



